Azure Key Vault Generate Password
- Nov 30, 2015 Now we have our password stored as a Secret in a Key Vault we can go ahead and use it in an ARM template. At present the way we supply Key Vault Secrets to ARM templates is via use of parameters file. We can feed in the Secret we pushed to our Key Vault using the below snippet in our parameters file.
- Creating a KeyVault secret in an existing keyvault. It will use your key vault not create new key vault. The following template works for me. (Add secrets to.
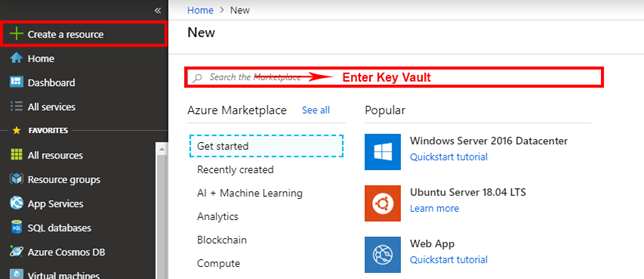
- Create a vault. Select the Create a resource option on the upper left-hand corner of the Azure portal. In the Search box, enter Key Vault. From the results list, choose Key Vault. On the Key Vault section, choose Create. On the Create key vault section provide the following information: Name: A unique name is required.
Use Azure Key Vault to encrypt keys and small secrets like passwords that use keys stored in hardware security modules (HSMs). For more assurance, import or generate keys in HSMs and Microsoft processes your keys in FIPS 140-2 Level 2 validated HSMs (hardware and firmware). With Key Vault, Microsoft doesn’t see or extract your keys. Note: It's possible to define Key Vault Access Policies both within the azurermkeyvault resource via the accesspolicy block and by using the azurermkeyvaultaccesspolicy resource.However it's not possible to use both methods to manage Access Policies within a KeyVault, since there'll be conflicts.
You can use PFX certificate’s along with Azure Key Vault in multiple ways, depending on your use case. You can import the PFX as a Key into Key Vault and use it just like you would use any other key or save it as a Secret and retrieve it as required. In this post I will explain how this is done.
Before I get into more details let’s take a moment to understand better the different file types used and what they represent.
CER: Contains the public part of the certificate and usually distributed outside.
PVK: Contains the Private key and securely stored
PFX: Usually has public, private keys, other certificate chains and password protected.
To create a test certificate for this sample I will use makecert and pvktopfx utilities. Alternatively, you could also use any existing certificate.
The -sky exchange sets the Subject Key Type to Exchange and allows encrypting/decrypting values using the certificate.
The makecert creates the CER and PVK, the public/private key files which gets combined into a single PFX file using pvktopfx.
Using the PFX Certificate to Encrypt and Decrypt
PFX files along with CER files allows to encrypt/decrypt data without the need for Key Vault. You can share the public key, CER, to your clients, who can then use it to encrypt data before sending it to the server. Using the private key, available in PFX, the server can decrypt this data
Creating a Key in Key Vault from PFX file
Now that I am able to use the PFX file (which essentially is a software-protected key) to encrypt/decrypt data, I will upload this to the Azure Key Vault so that it stays secure there. If you are new to Azure Key Vault and want to get started check my other posts.
To upload the PFX to Key Vault, you can use the Add-AzureKeyVaultKey PowerShell cmdlet and specify the PFX file path and password. Quickbooks 2010 payroll service key generator.
Using the unique key identifier, I can now access this key from PowerShell or using the Web API. You can still distribute the public key, CER, to your clients for encrypting the data and use the Azure Key Vault API to decrypt the data. Or use the Azure Key Vault to encrypt and decrypt the data.
The PFX file uploaded to the Key Vault is just like any other key vault key, the only difference being you give the public and private key. Once the key is created in Key Vault, the private part of the key stays secure within the Key Vault and is not accessible outside (except from the original PFX/PVK file).
Storing PFX file as a Secret
PFX files can also be stored as Secrets in Key Vault which allows you to retrieve and re-create the certificate as required. To add the certificate as a secret you can use the below PowerShell script (taken from here).
The script exports the certificate to a byte array and converts it to Base64 string representation and saves it to Key Vault as Secret using the Set-AzureKeyVaultSecret PowerShell cmdlet. You can export the certificate along with the password if required, so that when you recreate the certificate file, it will be password protected.
To retrieve and re-create the certificate you can either use PowerShell or API as shown below
You can use the PFX certificate as earlier as a file or a certificate object. These are the various ways that you can use PFX certificated along with Key Vault.
Hope this helps!
-->For added assurance, when you use Azure Key Vault, you can import or generate keys in hardware security modules (HSMs) that never leave the HSM boundary. This scenario is often referred to as bring your own key, or BYOK. Azure Key Vault uses nCipher nShield family of HSMs (FIPS 140-2 Level 2 validated) to protect your keys.
This functionality is not available for Azure China 21Vianet.
Note
For more information about Azure Key Vault, see What is Azure Key Vault?
For a getting started tutorial, which includes creating a key vault for HSM-protected keys, see What is Azure Key Vault?.
Supported HSMs
Transferring HSM-protected keys to Key Vault is supported via two different methods depending on the HSMs you use. Use the table below to determine which method should be used for your HSMs to generate, and then transfer your own HSM-protected keys to use with Azure Key Vault.
Azure Key Vault Generate Certificate Password
| Vendor Name | Vendor Type | Supported HSM models | Supported HSM-key transfer method |
|---|---|---|---|
| nCipher | Manufacturer |
| Use legacy BYOK method |
| Thales | Manufacturer |
| Use new BYOK method (preview) |
| Fortanix | HSM as a Service |
| Use new BYOK method (preview) |
Key Vault System
Next steps
Key Vault Xbox 360
Follow Key Vault Best Practices to ensure security, durability and monitoring for your keys.