Generate X 509 Certificate From Private Key
- X.509 Certificate Authority
- Generate X 509 Certificate From Private Key Search
- Generate X 509 Certificate From Private Keys
- X 509 Certificate Tutorial
Apr 17, 2016 Use the following lines to create your self-signed certificate: openssl genrsa 2048 private.key openssl req -new -x509 -nodes -sha1 -days 1000 -key private.key public.cer openssl pkcs12 -export -in public.cer -inkey private.key -out certkey.p12. The first line generates a new RSA 2048bit private key. 2048bit is required if you want to use.
X.509 Certificates
Public key certificates are a solution to the problem of identity. Encryption alone is enough to set up a secure connection, but there’s no guarantee that you are talking to the server that you think you are talking to. Without some means to verify the identity of a remote server, an attacker could still present itself as the remote server and then forward the secure connection onto the remote server. Public key certificates solve this problem.
- Jun 27, 2018 How to Create Certificates with XCA. Click Generate a new key. In the New Key window, enter a name for the certificate, select a key size, and then click Create. Configure the X.509 extensions. Click the Extensions tab. From the Type list, select Certification Authority.
- Sep 06, 2012 An X.509 certificate contains a private and a public key. As such it is suitable for password-less login via SSH. However, as always with certificates and keys and all that powerful stuff the handling of it all is very clumsy. Kingsley just explained how to setup SSH with X.509 certificates. I will try to add the missing pieces here.
- Of course the certificate returned by the CA does not contain a private key. But it is stored as.key file on the harddrive. The X509Certificate2 class has a property called PrivateKey which I guess will associate a private key with the certificate, but I can't find a way to set this property.
- Aug 07, 2018 In this article, I will be introducing you to a free X.509 certificate generator and key management software.XCA (X – Certificate and Key management) is a free software designed for Windows and Mac operating systems. This software is used to create and manage a database of private keys, X.509 certificates, certificate requests, and certificate revocation list (CRL).
The best way to think about public key certificates is as a passport system. Certificates are used to establish information about the bearer of that information in a way that is difficult to forge. This is why certificate verification is so important: accepting any certificate means that even an attacker’s certificate will be blindly accepted.
Using Keytool
Use the keytool version that comes with JDK 8:
X.509 Certificate Authority
The examples below use keytool 1.8 for marking a certificate for CA usage or for a hostname.
Generating a random password
Create a random password using pwgen (brew install pwgen if you’re on a Mac):
Server Configuration
You will need a server with a DNS hostname assigned, for hostname verification. In this example, we assume the hostname is example.com.
Generating a server CA
The first step is to create a certificate authority that will sign the example.com certificate. The root CA certificate has a couple of additional attributes (ca:true, keyCertSign) that mark it explicitly as a CA certificate, and will be kept in a trust store.
Generating example.com certificates
The example.com certificate is presented by the example.com server in the handshake.
You should see:
Mavis Beacon Teaches Typing Powered by UltraKey uses a success-based approach to typing instruction. This powerful and motivating way to learn provides a clear path to learning a new skill by setting personal goals and progressing along guided roadmaps. Just follow these seven easy. Mavis beacon product key generator.
Configuring example.com certificates in Nginx
If example.com does not use Java as a TLS termination point, and you are using nginx, you may need to export the certificates in PEM format.
Unfortunately, keytool does not export private key information, so openssl must be installed to pull private keys.
Now that you have both example.com.crt (the public key certificate) and example.com.key (the private key), you can set up an HTTPS server.
For example, to use the keys in nginx, you would set the following in nginx.conf:

If you are using client authentication (covered in Client Configuration below), you will also need to add:
You can check the certificate is what you expect by checking the server:
Client Configuration
There are two parts to setting up a client – configuring a trust store, and configuring client authentication.
Configuring a Trust Store
Any clients need to see that the server’s example.com certificate is trusted, but don’t need to see the private key. Generate a trust store which contains only the certificate and hand that out to clients. Many java clients prefer to have the trust store in JKS format.
You should see a trustedCertEntry for exampleca: Simple cipher encryption key generator.
The exampletrust.jks store will be used in the TrustManager.
Also see the Configuring Key Stores and Trust Stores section for more information.
Configure Client Authentication
Client authentication can be obscure and poorly documented, but it relies on the following steps:
- The server asks for a client certificate, presenting a CA that it expects a client certificate to be signed with. In this case,
CN=clientCA(see the debug example). - The client looks in the KeyManager for a certificate which is signed by
clientCA, usingchooseClientAliasandcertRequest.getAuthorities. - The KeyManager will return the
clientcertificate to the server. - The server will do an additional ClientKeyExchange in the handshake.
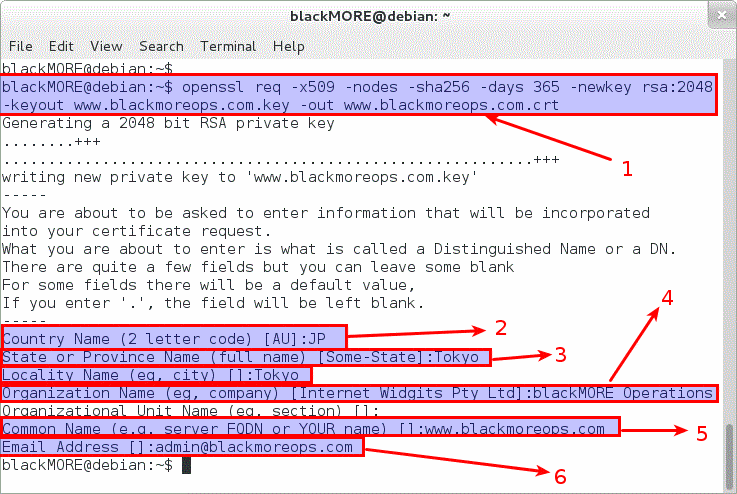
The steps to create a client CA and a signed client certificate are broadly similiar to the server certificate generation, but for convenience are presented in a single script:
There should be one alias client, looking like the following:
And put client.jks in the key manager:
Also see the Configuring Key Stores and Trust Stores section for more information.
Certificate Management Tools
If you want to examine certificates in a graphical tool than a command line tool, you can use Keystore Explorer or xca. Keystore Explorer is especially convenient as it recognizes JKS format. It works better as a manual installation, and requires some tweaking to the export policy.
If you want to use a command line tool with more flexibility than keytool, try java-keyutil, which understands multi-part PEM formatted certificates and JKS.
Certificate Settings
Secure
If you want the best security, consider using ECDSA as the signature algorithm (in keytool, this would be -sigalg EC). ECDSA is also known as “ECC SSL Certificate”.
Compatible
Generate X 509 Certificate From Private Key Search
For compatibility with older systems, use RSA with 2048 bit keys and SHA256 as the signature algorithm. If you are creating your own CA certificate, use 4096 bits for the root.
Generate X 509 Certificate From Private Keys
Further Reading
X 509 Certificate Tutorial
Next:Configuring Trust Stores and Key Stores